Secure your cloud with GDMS Network and Security Platform
GDMS as a VMware cloud service provider leverages network, and security platform NSX to provide secure networking services to its customers.
As companies in Myanmar and Laos increasingly turn to digital transformation via the cloud, they’re relying on partners like GDMS to help them migrate their apps and workloads to the cloud without sacrificing performance and mitigating risk.
By subscription to GDMS cloud services, you get access to the complete NSX suite giving you the possibility to centrally define, implement, and manage perimeter security gateway services, such as DNS, DHCP, and NAT. NSX allows customers to control North-South traffic quickly and easily without any hardware dependencies.
“Never Trust – Always Verify”
Security is an ongoing challenge for organizations with today’s dynamic and distributed workforce, growing BYOD, and the continued expansion into the cloud. While the cloud is often safer than a company’s own data center, it is still crucial for organizations to own and control who and what is allowed access to their applications and data – no matter where they are running.
With Zero-Trust, network security is set up to assume that you have already been compromised and any traffic, even behind the firewall, is considered “untrustworthy” until it’s proven to meet the right criteria.
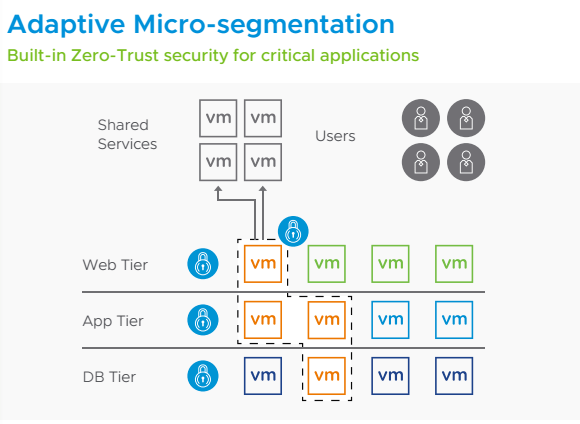
Inside your network perimeter or DMZ, smaller segments of the network are protected by their 4 own tiny perimeters (called a “micro perimeter”).
This allows a security administrator to add an extra layer of security around the company’s most important data, assets, applications, and services.
To access any individual segment in a Zero-Trust architecture, users must pass strict identity and device verification procedures. A “least-privilege” model is recommended, which limits access to only needed resources.
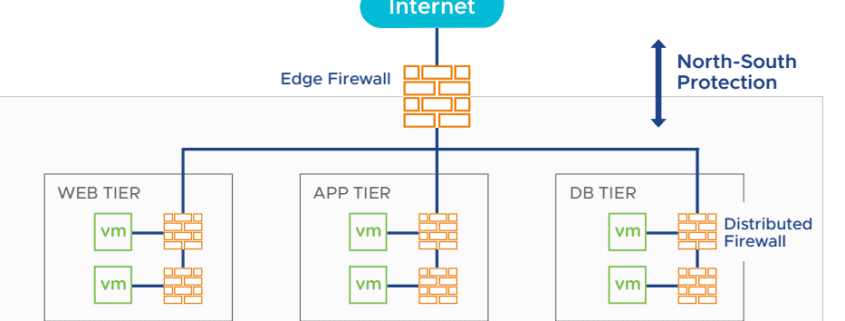
The first step in implementing a Zero-Trust network is to secure individual parts of the network using micro-segmentation. Micro-segmentation should be adopted in addition to network perimeter security controls. When you have both perimeter controls, as well as micro-segmentation, not only is traffic inspected and controlled as it enters your network (North-South), it’s also inspected as it moves laterally (East-West) between VMs and systems.
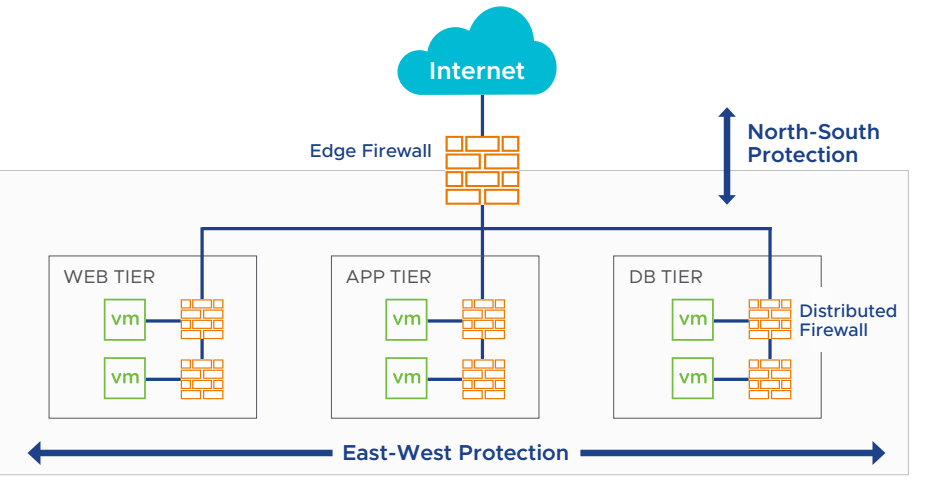
GDMS provides critical software-defined networking firewall capabilities for both perimeter,
or edge firewalls, as well as services for micro-segmentation, also known as distributed firewalls.
By offering these services at the software layer—decoupled from hardware—they are:
VMware Edge Gateway (ESG)
The ESG gives you access to all NSX Edge services such as firewall, NAT, DHCP, VPN, load balancing, and high availability. You can install multiple ESG virtual appliances in a data center.
GDMS offers a number of professional services to help you design and deploy your edge firewall. We can help with setting up least-privilege rules and other gateway configurations to support your Zero-Trust security goals.

Edge Gateways come in 4 sizes: Compact, Large, Quad-Large and X-Large.
Distributed Firewall
Micro-segmentation, also known as distributed firewalling (DFW), is an approach to defining network and security policies that allow organizations to segment and control workloads based on application profiles.
Distributed Firewalling is available with our cloud offering through either a self-service portal or as a managed service.
Features:
- Virtual firewalls embedded in the hypervisor
- No VM can circumvent the firewall (egress and ingress packets are always processed)
- Policies are attached to the VM for secure mobility
- Avoids routing traffic to the edge (and back) for inspection
- Inter-application routing improves app performance
Why Use GDMS Distributed Firewall:
- No “choke point” or single point of failure
- Based on software, it is easy to scale-out
- Enforcement as close to the VM as possible
- Enhanced context-aware protection for applications
As networks become virtualized and micro-segmentation becomes a strategic advantage for security teams, data inherently becomes segmented into buckets to allow teams greater visibility and control over information on the network. Segmentation can be used to separate day-to-day business data from sensitive or proprietary data.
From there, security and risk teams can place the proper security and access controls on sensitive data segments using micro-segmentation.
Enable network security controls
Network admins can more quickly identify and adjust privileges for certain data
types through micro-segmentation, enabling:
- Users to work with network data faster and more efficiently
- Increased agility and quick response to changing security needs
- Easier compliance with regulations
- Least-privilege enforcement
Achieve better data visibility and protection
If organizations understand where data exists, and which users are supposed to
have access to it, then:
- Data and services can be better monitored
- Data flows more quickly through an organization to the appropriate users
- Overall data security and agility improve
Stop lateral spread of threats
Network segmentation automatically interweaves connections and services to
create micro-perimeters around specific sets of data and information. This:
- Inhibits the spread of threats
- Accelerates identification and response to threats
- Minimizes impact of an attack
Layer 4 Protection
By default, our distributed firewalls offer protection up through layer 4 of the OSI
network stack, enabling:
- Users to work with network data faster and more efficiently
- Increased agility and quick response to changing security needs
- Easier compliance with regulations
- Least-privilege enforcement
Layer 7 Protection
Application context-aware
If organizations understand where data exists, and which users are supposed to
have access to it, then:
- Data and services can be better secured and monitored
- Overall data security and agility improve
Professional Services
GDMS offers professional and managed services to help you design, deploy, and manage your distributed firewalls.
- Assess on-premises networks, applications, and dependencies
- Design and deploy stretched networks for hybrid cloud/multi-cloud environments
- Define and implement firewall policies
- Migrate existing workloads/applications
- Transform security and networking to enable improved business agility and outcomes
Advanced Insights
GDMS offers additional advanced insights into traffic patterns to determine where you
can benefit the most from a context-aware firewall. This helps you to lower operational expenses
while focusing on these advanced capabilities where they’re needed most. This is available self-service or as a managed service.