VULNERABILITY SCANNING
Discover, analyze, and mitigate security flaws and vulnerabilities with our cloud-based vulnerability scanner.
Vulnerability scanning allow you to take a proactive approach to close any gaps and maintain a high level of security for your data, systems, employees, and customers.
Data breaches are often the result of outdated hardware or software equipment, unpatched vulnerabilities, so identifying and addressing these security gaps, eliminate that attack vector.
Continuous Risk Scanning
By using our cloud-based always-on risk scanning solution, you get a comprehensive high level view of your organization security posture. If a change is detected in your environment, you get immediately informed.
Online Vulnerability Scanner Features:
- Cloud-based solution with possibility to quickly deploy additional scanners inside your infrastructure
- Leading Scanner Solution: Scan more technologies and uncover more vulnerabilities than competing solutions
- Cost-effective solution: Adapted to your company size and budget
- Identifies the vulnerabilities that need attention with high-speed, accurate scanning, prioritize alerts based on the asset business value
- Benefit from Zero Day Research Team findings. Get immediate access to plugins to scan new vulnerabilities
Security Information and Event Management (SIEM)
A SIEM solution helps organizations to monitor threats across your IT environment in real time, allowing for early discovery of data breaches and targeted attacks.
Modern IT organizations are all equipped with a log event manager. But as the number of IT assets grow, it becomes harder and harder to read through the noise and identify patterns that can indicate that an attack is ongoing on your network.
A SIEM solution ingests high volume of data in seconds and help organizations identify unusual behavior, offering real time protection for businesses.
SIEM Top Features:
- Continuous monitoring of events, conditions, and critical KPIs
- Reports can be created in real time, scheduled to run at any interval and used in your dashboards
- Complete utilization of metrics data to boost search performance and save in data storage costs
- Pre-built machine learning analytics for identified use cases
- Maximize data management flexibility while maintaining search performance
- Policy-based mechanism that enables you to reserve system resources (e.g. CPU and memory) for ingestion and search workloads
- SAML integration for single sign-on through most popular identity providers
-
Industry-certified, customer trusted (ISO 27001, SOC 2 Type 2, GDPR, PCI DSS, HIPAA, FedRAMP)
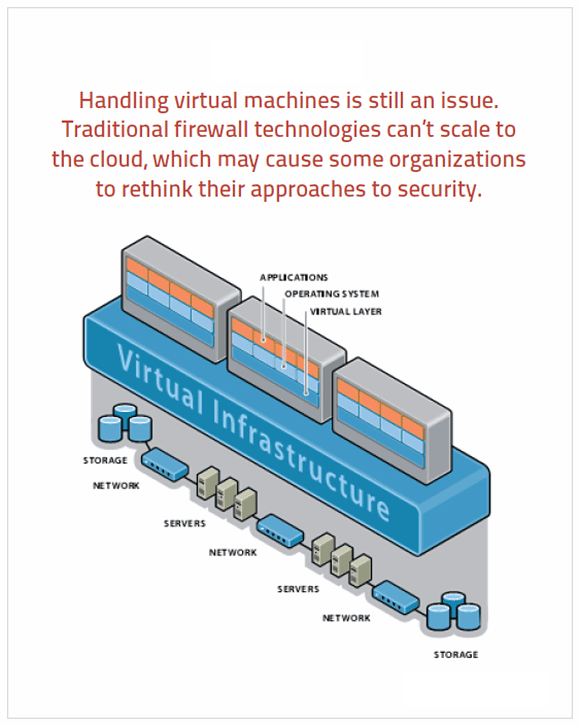
Managed Next Generation Firewall (NGFW)
Next Generation Firewalls deliver best-in-class enterprise security for any organization at any scale with holistic visibility and real-time threat protection. Organizations can embed security deep into the hybrid IT architecture and build security-oriented networks.
GDMS Cloud Based Managed Firewall allows organizations to deploy perimeter firewalls in minutes to protect their IT environment in the cloud or on-premises.
NGFW Top Features
Web Application Security Scanner
Even the best web application, developed by the most security-centric developers, is going to present security risks. It’s simply unavoidable.
Developer main focus is to translate business requirement into functionality, security comes always second.
As new features are designed and deployed into production, it is no surprise to find critical vulnerabilities in the application code.
Performing a continuous security check is crucial to ensure your web application does not expose sensitive data.
Web Application Security Scanner Top Features
- Crawls all web pages, including those built in HTML5 and JavaScript
- Acts as a Java vulnerability scanner by examining web applications built with popular frameworks including Java frameworks
- Inspects the the source code of a web application whilst it is in execution
- Replicates user actions to execute scripts just like a browser
- Login Sequence Recorder allows you scan password-protected pages automatically
- Discover critical vulnerabilities such as SQL injection and command injection
- Identifies TLS/SSL vulnerabilities, web server vulnerabilities and other misconfigurations
- Performs a WordPress security scan to identify vulnerabilities in WordPress
- Integrates with web application firewalls and automatically creates protective rules
- Integrates with Issue Trackers such as Atlassian Jira, GitHub, GitLab, Microsoft TFS, Bugzilla, and Mantis
Risk Security Monitoring
Time is a valuable commodity in cybersecurity. With our digital risk monitoring solution, you can automate your digital risk management and receive insight about any significant changes to your security posture related to Dark Web, data breaches, compromised credentials, network infections, and other security incidents.
Digital Risk Monitoring Top Features
- In-depth risk evaluation throughout the entire enterprise ecosystem.
- Monitor digital footprints of any size on a massive scale.
- Proactively enable strategic actions to improve security.
- Identify low, medium, and high-risk areas for managing your infrastructure, network resources, and other company assets.
- SaaS Solution deployed in minutes, receive instantaneous insights on your security posture